Voice cloning technology, powered by artificial intelligence, is rapidly evolving, offering both exciting possibilities and complex ethical considerations. This comprehensive guide delves into the intricacies of voice cloning, exploring its technical underpinnings, potential applications, and crucial ethical safeguards necessary to ensure responsible development and deployment. We will examine the various methods used to create digital voice replicas, the potential for misuse, and the critical need for ethical guidelines.
From the technical aspects of audio processing and machine learning algorithms to the legal and ethical implications, this resource provides a structured framework for understanding voice cloning in a responsible light. We will also analyze the challenges surrounding intellectual property rights, user consent, and data security. The aim is to equip readers with a thorough understanding of the technology and the necessary precautions to prevent misuse.
Introduction to Voice Cloning with AI

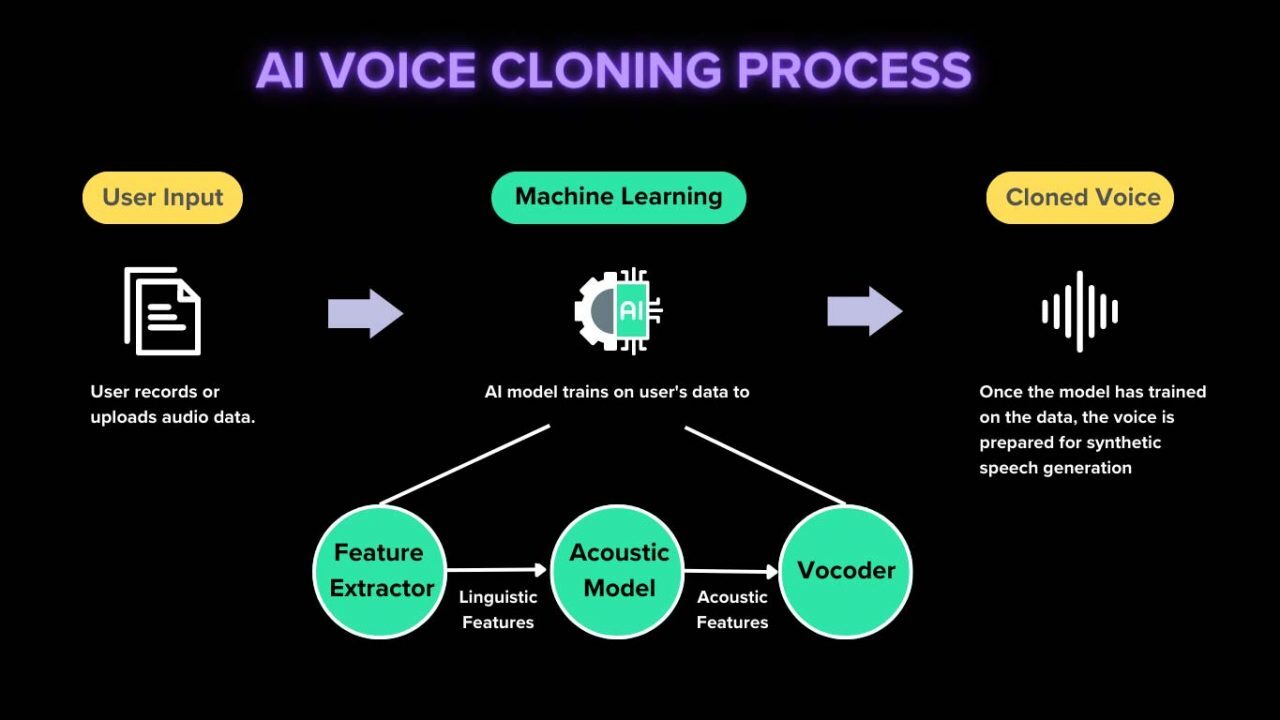
Voice cloning technology, powered by artificial intelligence, has rapidly advanced, enabling the creation of highly realistic digital voice replicas. This technology leverages sophisticated algorithms to analyze and synthesize speech patterns, allowing for the generation of a voice that closely mimics a specific individual’s vocal characteristics. This process is not limited to simple sound reproduction; it delves into the nuances of intonation, rhythm, and even emotional expression.This detailed exploration will illuminate the fundamental processes of voice cloning, the different methodologies employed, and the technical underpinnings of this fascinating technology.
We will also examine the potential applications and ethical considerations surrounding this innovative field.
Fundamental Processes in Voice Cloning
Voice cloning involves a multi-step process. First, a significant amount of audio data from the target speaker is required. This data forms the basis for the algorithm to learn the speaker’s unique vocal characteristics. Subsequently, advanced machine learning algorithms analyze this data, identifying patterns in the speaker’s pronunciation, intonation, and rhythm. These algorithms then generate a mathematical model of the speaker’s voice, effectively creating a digital representation of their vocal tract and articulatory movements.
Finally, this model is used to synthesize new speech, replicating the speaker’s voice with remarkable accuracy.
Different Types of Voice Cloning Methods
Several methods exist for creating voice clones. These methods vary in their complexity and the level of detail they capture.
| Method | Description | Example |
|---|---|---|
| WaveNet | This method uses a neural network to learn the probability distribution of the audio waveform. It creates a model of the voice by predicting the next audio sample in a sequence, based on the previous samples. | Creating a realistic voice that can mimic the nuances of a specific speaker’s pronunciation and intonation. |
| Tacotron 2 | This approach combines a neural network for text-to-speech synthesis with another network that learns to predict the mel-spectrogram, a representation of the audio signal. | Synthesizing a natural-sounding voice from text input, effectively replicating the speaker’s vocal qualities. |
| Speaker Embedding | This method focuses on extracting the unique characteristics of a speaker’s voice through mathematical embeddings. These embeddings capture the essence of the voice without relying on raw audio waveform. | Creating a voice clone that mimics the speaker’s intonation and stress patterns, potentially using a smaller dataset. |
Technical Aspects of Voice Cloning
The technical aspects of voice cloning involve sophisticated audio processing and machine learning algorithms. Audio processing techniques are employed to clean and pre-process the input audio data, removing background noise and artifacts. Machine learning algorithms, such as recurrent neural networks (RNNs) and generative adversarial networks (GANs), play a critical role in modeling the speaker’s voice and generating new speech.
These algorithms learn from the input data to create a model that captures the unique characteristics of the speaker’s voice, enabling the creation of realistic voice clones. For instance, GANs can be used to train a model that distinguishes between real and synthetic speech, allowing the system to improve the realism of the cloned voice.
Ethical Considerations of Voice Cloning
Voice cloning technology, while offering exciting possibilities, presents a complex array of ethical dilemmas. Its potential for misuse demands careful consideration and proactive measures to prevent harm. The ease with which authentic-sounding voices can be replicated necessitates a framework for responsible development and deployment.The potential for malicious use of this technology is significant. It’s crucial to acknowledge the risks associated with this technology and to establish clear guidelines for its development and application to prevent harm.
Understanding the ethical concerns and implementing safeguards are essential to harness the benefits of voice cloning while mitigating its risks.
Potential Ethical Dilemmas
The development and application of voice cloning technology raise several ethical concerns. These include issues surrounding privacy, security, and the potential for manipulation and fraud. The ability to replicate a person’s voice raises profound questions about identity and authenticity in the digital age. Furthermore, the potential for misuse, particularly in areas like impersonation and fraud, underscores the need for stringent regulations and safeguards.
Misuse of Voice Cloning Technology
Voice cloning technology, if not used responsibly, can be exploited for various malicious purposes. One prominent concern is impersonation, where a cloned voice can be used to deceive individuals for financial gain or to spread misinformation. For example, a cloned voice could be used to make fraudulent calls, impersonating a bank official or other trusted authority figure. The potential for identity theft and financial fraud is significant, impacting both individuals and institutions.
Impact on Privacy and Security
The proliferation of voice cloning technology has profound implications for individual privacy and security. The ability to replicate a voice without the speaker’s consent raises concerns about the potential for unauthorized recordings and misuse of personal data. The ease of replication could lead to the dissemination of private conversations or the creation of deepfakes, blurring the lines between reality and fabrication.
Comparison with Other Forms of Digital Impersonation
Voice cloning shares similarities with other forms of digital impersonation, such as deepfakes and synthetic media. However, voice cloning specifically targets the auditory modality, potentially creating a more convincing form of impersonation. The ease of replication and the potential for audio manipulation create a unique set of challenges that require specific countermeasures.
Legal Implications of Voice Cloning
The legal implications of voice cloning are still evolving, but several jurisdictions are beginning to address the issues raised by this technology. Current laws governing intellectual property, defamation, and fraud may need to be adapted to account for the unique characteristics of voice cloning. Legal frameworks need to be developed that address issues of consent, ownership, and liability in cases of misuse.
Ethical Concerns, Potential Abuses, and Suggested Safeguards
| Ethical Concern | Potential Abuse | Suggested Safeguards |
|---|---|---|
| Privacy | Unauthorized voice recordings and misuse of personal data | Implementing strong encryption and access controls for voice data; obtaining informed consent for voice cloning; establishing clear guidelines for data handling. |
| Security | Fraudulent activities, identity theft, and impersonation | Developing robust authentication protocols for voice cloning services; implementing tools to detect cloned voices; establishing legal frameworks to hold perpetrators accountable. |
| Authenticity | Spread of misinformation and manipulation | Promoting media literacy and critical thinking skills; developing technologies to distinguish between authentic and cloned voices; establishing clear guidelines for the use of voice cloning in media. |
| Consent | Voice cloning without consent of the original speaker | Requiring explicit consent for voice cloning; implementing mechanisms for revoking consent; ensuring transparency in the use of voice cloning. |
Safeguarding Against Malicious Use

Voice cloning technology, while offering exciting possibilities, necessitates robust safeguards to prevent misuse. Malicious actors could exploit this technology for fraudulent activities, impersonation, and the spread of misinformation. Proactive measures are crucial to mitigate these risks and maintain public trust in the technology.Preventing malicious use involves a multi-faceted approach encompassing technological solutions, legal frameworks, and public awareness initiatives.
By implementing appropriate security protocols and promoting responsible use, we can strive towards a future where the benefits of voice cloning are realized without jeopardizing the integrity of communication.
Authentication Techniques for Verified Voices
Verifying the authenticity of a voice is paramount to combatting fraudulent voice cloning. Robust authentication techniques are essential to distinguish between genuine and cloned voices. These techniques should be designed to withstand sophisticated attacks and maintain the highest levels of accuracy.Multi-factor authentication (MFA) plays a critical role in verifying the identity of the speaker. Combining knowledge-based factors (e.g., passwords, PINs) with possession-based factors (e.g., security tokens, smart cards) significantly strengthens the verification process.
Biometric authentication methods, such as voice recognition and facial recognition, can further enhance the security posture. These techniques are effective at differentiating genuine from fraudulent voices.
Strategies for Detecting and Reporting Fraudulent Activity
Detecting fraudulent voice cloning activity requires a combination of advanced algorithms and vigilant monitoring. Systems capable of identifying subtle discrepancies in speech patterns, intonation, and rhythm can be instrumental in flagging potential instances of cloning.Regularly monitoring communication channels for unusual or suspicious patterns is vital. For instance, sudden changes in the volume, tone, or pitch of a speaker’s voice could trigger alerts.
Implementing sophisticated machine learning models can further aid in the detection process.Furthermore, creating dedicated channels for reporting suspected fraudulent voice cloning activities is crucial. These reporting mechanisms should be easily accessible and user-friendly, encouraging users to promptly flag potential instances of impersonation. Users should be provided with clear guidelines on how to report suspected fraudulent activities.
Procedures for Suspected Fraudulent Voice Cloning Attempts
If a fraudulent voice cloning attempt is suspected, a predefined procedure should be implemented to address the situation effectively. This involves a systematic approach to investigation, containment, and remediation.
- Initial Assessment: Immediately upon suspicion, gather all available evidence related to the alleged fraudulent activity, such as audio recordings, timestamps, and communication logs. This initial step is crucial to understanding the nature and scope of the potential issue.
- Verification and Analysis: Employ specialized tools and techniques to analyze the voice samples and determine the authenticity of the voice. This analysis should include examining for discrepancies in speech patterns and comparing with known authentic voice samples.
- Reporting and Escalation: Report the suspected fraudulent activity to the appropriate authorities or platforms. Formal reporting mechanisms should be in place to ensure proper escalation and investigation.
- Containment and Remediation: Implement measures to contain the spread of misinformation or fraudulent communication. This might involve issuing warnings, suspending accounts, or taking other necessary steps to mitigate the impact of the cloning activity.
Potential Safeguards and Measures
Implementing a range of safeguards can help mitigate the risk of malicious voice cloning. These measures should be designed to be robust, scalable, and adaptable to evolving technologies.
- Secure Cloud Storage: Data should be stored in encrypted cloud storage solutions with access controls to limit unauthorized access. This helps safeguard the sensitive data that could be used for voice cloning.
- Advanced Voice Recognition Systems: Implementing advanced voice recognition systems that can differentiate between genuine and cloned voices is crucial to deter fraudulent activities. Regular updates and enhancements are needed to keep up with the ever-evolving techniques used in voice cloning.
- User Education and Awareness Programs: Educating users about the risks of voice cloning and the importance of verifying the authenticity of voices is essential. This includes providing training materials and guidelines on recognizing suspicious voice patterns and reporting fraudulent activities.
- International Collaboration and Standards: Collaboration between nations and industry players to develop shared standards and protocols for voice cloning authentication is necessary. This ensures a uniform approach to safeguarding against malicious use of this technology.
Applications of Ethical Voice Cloning

Voice cloning technology, when implemented responsibly and ethically, offers a wealth of potential benefits across various sectors. Its ability to replicate and manipulate human speech opens doors to innovative solutions for accessibility, communication, and creative expression. Careful consideration of ethical implications and security measures is paramount to ensure its responsible use.Voice cloning, in its ethical applications, allows for the creation of personalized and accessible communication experiences, and opens creative avenues for entertainment and art.
These applications extend beyond mere replication, offering unique solutions tailored to specific needs. The careful implementation of voice cloning, with strict adherence to ethical guidelines, is key to maximizing its potential while minimizing potential risks.
Accessibility for Speech-Impaired Individuals
Voice cloning can provide substantial support for individuals with speech impairments. Speech-generating devices often struggle with nuances and complexities of human speech. Voice cloning, utilizing a pre-existing voice sample, can replicate the user’s speech more accurately, resulting in smoother, more natural communication. This enhanced realism improves communication effectiveness and facilitates more natural interaction with others. For instance, individuals with cerebral palsy or other neuromuscular disorders can use voice cloning to communicate more effectively with family, friends, and colleagues.
Communication Enhancement in Diverse Settings
Voice cloning can enhance communication in various settings. In customer service, voice cloning can be used to provide a consistent and personalized experience. This can involve having a pre-recorded greeting in a specific voice, or even a customer representative with a personalized voice. In education, voice cloning can be used to create engaging learning materials. A teacher’s voice, for example, can be used to narrate educational content, or even recreate classroom lectures, preserving valuable teaching moments.
Creative Applications in Art, Music, and Entertainment
Voice cloning presents exciting creative possibilities in art, music, and entertainment. Artists can use it to create unique soundscapes and virtual characters. Music producers can use the technology to experiment with different vocal styles, potentially expanding the range of available sounds. For instance, voice cloning can help recreate historical figures’ voices, enhancing historical documentaries and educational content.
In gaming, voice cloning can create realistic character voices and interactive storytelling experiences.
Table of Ethical Applications of Voice Cloning
| Application | Benefits | Considerations |
|---|---|---|
| Accessibility for Speech-Impaired Individuals | Improved communication, more natural interaction, increased independence. | Maintaining the authenticity and individuality of the original voice, ensuring data privacy and security. |
| Communication Enhancement in Diverse Settings | Consistent and personalized customer service, enhanced educational resources, accessible information dissemination. | Ensuring the cloned voice aligns with brand identity and customer expectations, protecting against impersonation and misuse. |
| Creative Applications in Art, Music, and Entertainment | Unique soundscapes, virtual characters, recreating historical voices, immersive experiences. | Respecting intellectual property rights, avoiding misrepresentation of individuals, ensuring the cloned voice does not mislead or harm. |
Voice Cloning and Intellectual Property
Voice cloning technology, while offering exciting possibilities, raises significant concerns regarding intellectual property rights. The ability to replicate a voice with remarkable accuracy necessitates a careful examination of existing legal frameworks and the potential for misuse. This section will explore the impact of voice cloning on copyright and intellectual property, highlighting potential infringements and the need for clear guidelines.Voice cloning techniques can potentially infringe upon intellectual property rights, particularly in contexts where a voice is uniquely associated with a creative work or a brand.
This includes recordings of music, audiobooks, podcasts, and even voiceovers for commercials. If a voice is cloned without permission from the original owner, this could lead to legal disputes and challenges in determining ownership and usage rights. The technology’s advancement has brought the need for stronger protection for creators and owners of unique voices into sharper focus.
Impact on Copyright and Intellectual Property Rights
Voice cloning can potentially infringe on various intellectual property rights, including copyright and trademarks. If a voice is uniquely associated with a particular brand or creative work, unauthorized cloning could lead to confusion, dilution, or misappropriation of the original content. This is especially relevant for voice-based media, where the voice itself can be a significant element of the creative expression.
Scenarios of Infringement
Unauthorized use of a cloned voice for commercial purposes or to create derivative works without permission from the original voice owner constitutes infringement. This can include using a cloned voice to create counterfeit audiobooks, impersonate a public figure for malicious purposes, or even to generate fraudulent content. Further, the potential for cloning to be used to impersonate someone for financial gain or to spread misinformation adds a layer of concern regarding the misuse of this technology.
Legal Frameworks and Guidelines
Current legal frameworks governing intellectual property rights may not adequately address the complexities introduced by voice cloning technology. Existing copyright laws often focus on the expression of an idea rather than the voice itself, which can lead to ambiguity and difficulties in enforcement. The need for clear guidelines on ownership and usage rights for cloned voices is paramount to prevent misuse and protect creators.
Ownership and Usage Rights
The development of clear guidelines regarding ownership and usage rights is crucial. Such guidelines should address the rights of the original voice owner, including the exclusive right to use, reproduce, and distribute the voice in various forms. It should also define the boundaries of permissible use and reproduction for third parties.
Examples of Cases
While no definitive legal precedents specifically addressing voice cloning exist yet, cases involving voice imitation and impersonation have been litigated in the past. These cases highlight the need for legal clarity and the potential for future disputes. As the technology advances and more instances of voice cloning emerge, these precedents will play an increasingly important role in shaping future legal interpretations and frameworks.
Comparison of Voice Cloning Techniques and Copyright Impacts
| Voice Cloning Technique | Potential Impact on Copyright |
|---|---|
| Deepfake-based voice cloning | High potential for copyright infringement if used without permission. The ability to create convincing imitations significantly increases the risk of misuse. |
| Speaker Embeddings | Copyright infringement can arise when the embeddings are used to generate content that is indistinguishable from the original voice, without authorization. |
| WaveNet-based voice cloning | Potential for copyright infringement is high. The precision of the cloning process can lead to an indistinguishable replica of the original voice. |
User Consent and Data Security
Ethical voice cloning necessitates a robust framework for user consent and data security. A critical component of responsible AI development is ensuring that users understand the implications of their voice data being used for cloning and are empowered to make informed choices. Prioritizing data security is paramount to preventing misuse and maintaining user trust.Data security and user consent are intertwined.
Users must provide explicit and informed consent for their voice data to be used in the voice cloning process. Robust data security measures must be implemented to protect the privacy and integrity of the data throughout its lifecycle.
Importance of Informed Consent
User consent is crucial to ensure that voice cloning is conducted ethically. Users must understand the intended purpose of the voice cloning, how their data will be used, and the potential risks associated with this process. This includes a clear explanation of data retention policies, data sharing practices, and how user privacy will be protected. Informed consent is not just a legal requirement; it is a cornerstone of responsible AI development.
Data Security Measures
Protecting user data during the voice cloning process necessitates multiple layers of security. This includes encrypting the data both in transit and at rest, implementing robust access controls to limit access to sensitive information, and utilizing strong authentication methods. Data anonymization techniques should also be considered to further protect user identity.
Transparency in Data Handling and Usage
Transparency in data handling and usage builds user trust. Clearly articulating how voice data will be used, stored, and protected is essential. Users should be informed about the specific algorithms used for voice cloning and the limitations of these technologies. Detailed information about data retention policies, including timelines and criteria for data deletion, should be readily available to users.
Secure Storage and Handling of Voice Data
Secure storage and handling of voice data are paramount. This involves using secure servers with robust physical and digital security measures. Regular audits of the systems should be conducted to ensure the continued integrity of the data. Strict adherence to data protection regulations, such as GDPR, is essential.
Best Practices for Obtaining Consent and Safeguarding User Data
Implementing best practices for obtaining consent and safeguarding user data is vital. These include using clear and concise language in consent forms, providing multiple channels for users to express their consent, and offering options for users to withdraw their consent at any time. Regularly reviewing and updating policies and procedures to reflect evolving technologies and regulations is also a key element.
Examples of Best Practices
Examples of best practices include pre-recorded videos or interactive tutorials explaining the process of voice cloning and its implications, allowing users to preview the cloned voice before finalizing their consent, and offering a user-friendly dashboard for managing their voice data, including options to download, delete, or update consent.
User Consent Procedures and Data Security Measures
| Consent Procedure | Data Security Measure |
|---|---|
| Clear and concise consent forms | Data encryption (both in transit and at rest) |
| Multiple consent channels (e.g., online forms, email) | Robust access controls |
| Detailed explanation of data usage | Regular security audits |
| Provision for withdrawal of consent | Data anonymization techniques |
| User-friendly data management dashboard | Adherence to data protection regulations (e.g., GDPR) |
Future Trends and Innovations
Voice cloning technology is rapidly evolving, driven by advancements in artificial intelligence and machine learning. This dynamic field promises significant advancements in various sectors, from entertainment and communication to customer service and healthcare. However, ethical considerations and potential risks remain crucial factors to address as the technology matures.
Emerging Technologies in Voice Cloning
Deep learning models, particularly Generative Adversarial Networks (GANs), are at the forefront of voice cloning advancements. These models learn complex patterns in speech data to create highly realistic synthetic voices. Researchers are continuously refining these models, leading to improved accuracy and naturalness in the generated speech. Beyond GANs, other innovative approaches, such as transformer networks, are being explored for their potential to further enhance the quality and control of voice cloning.
Future Advancements and Possibilities
The potential applications of advanced voice cloning extend far beyond current capabilities. Future advancements may enable more nuanced and personalized voice cloning, allowing for the creation of voices that mirror specific emotional states or accents. This could revolutionize voice acting, creating more immersive and personalized experiences in games and virtual reality environments. Additionally, improvements in voice cloning technology could lead to more accurate and efficient transcription services.
Impact on Various Industries
Voice cloning is poised to transform numerous industries. In customer service, automated voice assistants could provide more personalized and empathetic interactions. In entertainment, voice cloning will likely play a significant role in creating realistic virtual characters and interactive storytelling experiences. Healthcare could benefit from more accessible and efficient communication tools, allowing for remote consultations and personalized medical advice.
Predictions on Technological Evolution
The evolution of voice cloning is likely to involve increased sophistication in model training and data handling. Researchers will likely focus on developing more robust and secure methods for voice cloning, minimizing the potential for misuse. There is potential for improved control over the generated voice characteristics, allowing for finer tuning of speech parameters such as tone, rhythm, and emotional inflection.
Timeline of Potential Innovations
| Year | Potential Innovation |
|---|---|
| 2024-2025 | Improved voice cloning models with enhanced naturalness and control. |
| 2026-2027 | Development of personalized voice cloning that replicates specific emotional states and accents. |
| 2028-2029 | Integration of voice cloning technology into customer service platforms, creating more personalized and empathetic interactions. |
| 2030-2031 | Enhanced voice cloning capabilities for virtual characters in gaming and virtual reality environments. |
| 2032-2033 | Application of voice cloning in healthcare, enabling more accessible and efficient remote consultations and personalized medical advice. |
Potential Benefits and Risks
The potential benefits of voice cloning are significant, ranging from more personalized customer service to groundbreaking advancements in entertainment and healthcare. However, it’s crucial to acknowledge the potential risks, including the misuse of voice cloning for fraudulent activities or impersonation. Developing robust safeguards and ethical guidelines will be critical to ensure the responsible use of this transformative technology.
Summary
In conclusion, voice cloning with AI presents a powerful technology with multifaceted applications, but also significant ethical and legal considerations. By carefully considering the ethical implications, implementing robust safeguards against misuse, and adhering to clear guidelines regarding user consent and data security, we can harness the benefits of voice cloning while mitigating potential risks. This exploration of responsible voice cloning practices is essential for navigating the future of this transformative technology.